Hi everyone,
Hope you’re doing good!
In my last blog post I explained how to update Oracle Enterprise Manager and its OEM Agents from RU 13.5.0.16 to RU 13.5.0.20. You can check it here:
How to Update Oracle Enterprise Manager from RU 13.5.0.16 to RU 13.5.0.20
In the blog post described above, one of the required steps is to apply Release Update 13.5.0.20 on OEM Agents after Release Update is applied on OEM.
One of the tasks when you are updating your OEM stack is to apply the patch on OEM Agents, and usually, the prerequisite is to have the latest version of AgentPatcher, which I show how to update in the mentioned blog post. I also wrote a blog post showing how to update AgentPatcher using an Ansible Playbook, so you can speedup this action by running the Ansible playbook against all the servers where you need to update the OEM Agent. You can see about this Ansible Playbook here:
Ansible Playbook to Update AgentPatcher on OEM Agents
We do know that after update the AgentPatcher, we can apply the RU 13.5.0.20 on OEM Agents using the Patches & Updates features of Oracle Enterprise Manager, which I am actually showing how to do it in the first blog post mentioned here. This feature, Patches & Updates, works very well, but, sometimes, you need to confirm the version of RU you are running on your OEM Agents. For example, to confirm the RU version we are running after the patch. In a very simple way, we can do it using the following command with the user whom is the owner of OEM agent on your server:
ORACLE_HOME=$(ps -ef |grep ’emwd.pl agent’ | grep -v grep | awk ‘{print $8}’ | sed ‘s/\/perl\/bin\/perl//g’)
${ORACLE_HOME}/AgentPatcher/agentpatcher lspatches | grep ‘oracle.sysman.top.agent/13.’ | awk ‘{for (i=5; i<=NF; i++) printf “%s “, $i; printf “\n”}’
Oracle Enterprise Manager 13c Release 5 Platform Update 20 (13.5.0.20) for Oracle Management Agent
Perfect! But just imagine we have lot’s of servers to do it. It will be really bad to spend some time to do it manually, isn’t?
If your company use Ansible, you can automate this. I will share on this blog post a simple Ansible Playbook to perform this task. So, with Ansible, does not matter if you have one server or thousands servers to perform the activity. The time you will spend it should be roughly the same!
Note: this playbook is a “version 0” of it. Basically, the only Ansible module I’m using here is shell.
I will not explain the files shared below in detail, mostly of them are self-explained. Files ansible.cfg and check_Agent_Patch.yml have some parameters required by Ansible, I encourage you to read the Ansible documentation for more details. It will be a pleasure if I can help with some question, but please, keep in mind, I am not a huge expert on Ansible!
Below we have the basic folder structure for this playbook:
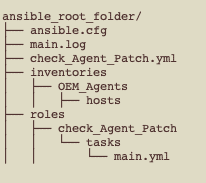
Explaining just a little bit the folder structure described above:
- ansible.cfg: basic parameters for Ansible. On this file we describe what will be the log file name, what is the user that will connect through SSH from Ansible Server to Servers where we have OEM Agents running, and some others parameters;
- main.log: the execution log;
- check_Agent_patch.yml: the playbook file, on this file, we have some others parameters that Ansible will use and what roles Ansible will execute, on this case, Ansible will only execute a role called check_Agent_Patch;
- inventories/OEM_Agents/hosts: the list of hosts where Ansible must connect to perform the activities;
- roles/check_Agent_Patch/tasks/main.yml: all the tasks that role check_Agent_Patch will perform.
So, below, we’ll have the full content of every file described above except by the log file.
ansible.cfg:
[defaults]
# output
display_skipped_hosts = no
stdout_callback = default
# allow new fingerprints
host_key_checking = false
# inventory
inventory = inventories/OEM_Agents/hosts
# logging
log_path = main.log
# retry
retry_files_enabled = False
# default ssh user
remote_user = svc_ansible
# general settings
timeout = 120
forks = 50
[ssh_connection]
pipelining = true
scp_if_ssh = true
check_Agent_Patch:
---
- hosts: all
gather_facts: true
any_errors_fatal: true
become: true
pre_tasks:
roles:
- { role: check_Agent_Patch }
inventories/OEM_Agents/hosts:
SERVER01
SERVER02
SERVER03
SERVER04
SERVER05
SERVER06
SERVER07
SERVER08
SERVER09
SERVER10
SERVER11
SERVER12
SERVER13
SERVER14
SERVER15
SERVER16
SERVER17
SERVER18
SERVER19
SERVER20
SERVER21
SERVER22
SERVER23
SERVER24
SERVER25
SERVER26
SERVER27
SERVER28
OEM-01
roles/check_Agent_Patch/tasks/main.yml:
---
- name: get the AGENT_OWNER
shell: |
ps -ef |grep agent_13 | grep -v grep | grep emw | awk '{print $1}'
register: agent_owner_ps
become_user: root
- name: get the AGENT_HOME
shell: |
ps -ef |grep 'emwd.pl agent' | grep -v grep | awk '{print $8}' | sed 's/\/perl\/bin\/perl//g
register: agent_home_ps
become_user: root
- name: set facts
set_fact:
agent_home: '{{ agent_home_ps.stdout }}'
agent_owner: '{{ agent_owner_ps.stdout }}'
- name: get the main patch applied
shell: |
${ORACLE_HOME}/AgentPatcher/agentpatcher lspatches | grep 'oracle.sysman.top.agent/13.' | awk '{for (i=5; i<=NF; i++) printf "%s ", $i; printf "\n"}
environment:
ORACLE_HOME: "{{ agent_home }}"
PATH: "{{ agent_home }}/bin;/usr/local/bin:/bin:/usr/bin:/usr/local/sbin:/usr/sbin"
register: agentpatcher_lspatches
become_user: "{{ agent_owner }}"
- name: show the main patch applied on Agent
debug:
msg: "{{ agentpatcher_lspatches.stdout }}"
As you can see in the above file, I am setting the owner for OEM Agent based on process running on OS, getting the ORACLE_HOME for agent, running agentpatcher utility and saving the output in a variable called agentpatcher_lspatches, and as the last step, displaying the output for this variable.
To execute the playbook you can first set which ansible.cfg you would like to use. We’ll use the same file we have in our directory.
Below I am showing how to execute the playbook and also showing a small piece of the execution (just to make easier to read):
export ANSIBLE_CONFIG=`pwd`/ansible.cfg
ansible-playbook check_Agent_Patch.yml
TASK [update_AgentPatcher : show the new version of AgentPatcher] ************************************************
ok: [SERVER01] => {
“msg”: “Oracle Enterprise Manager 13c Release 5 Platform Update 20 (13.5.0.20) for Oracle Management Agent”
}
ok: [SERVER02] => {
“msg”: “Oracle Enterprise Manager 13c Release 5 Platform Update 20 (13.5.0.20) for Oracle Management Agent”
}
ok: [SERVER03] => {
“msg”: “Oracle Enterprise Manager 13c Release 5 Platform Update 20 (13.5.0.20) for Oracle Management Agent”
}
PLAY RECAP *******************************************************************************************************
SERVER01 : ok=9 changed=5 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
SERVER02 : ok=9 changed=5 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
SERVER03 : ok=9 changed=5 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
PS: the playbook will only return values if you already have any RU installed on your agent. If you don’t have any RU installed, the return will be in blank.
Hope this helps!
Peace!
Vinicius
Related posts
About

Disclaimer
My postings reflect my own views and do not necessarily represent the views of my employer, Accenture.



